Summary
A bastion service is an OCI service that allows secure and managed access to resources within a private subnet using SSH or SSH tunneling
Reference
OCI Bastion Service
Traditional Bastion
- Linux or Window instance placed in a DMZ subnet
- Forward connections from Internet to private networks
- Needs a public IP
- Cannot be deployed in private subnets and security zones
Also known as a Jump Host.
Challenges with Traditional Bastion
- Security
- Scale and Performance
- Disaster Recovery
- Cost
OCI Bastion
- No Public IP needed
- AuthZ through IAM policies
- Managed by OCI
- Added scurity with CIDR block allowlist
- Time-limited access to targt resource
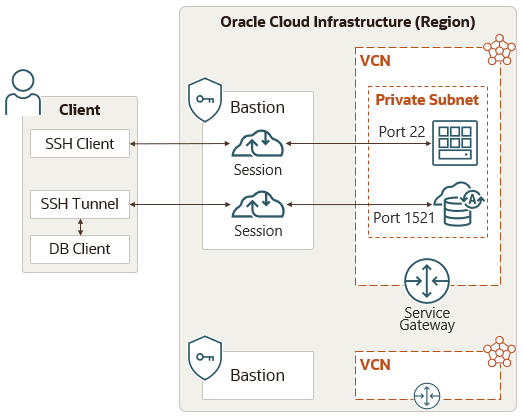
OCI Bastion Service Network Architecture
- Private endpoint connects to target subnets
- Target subnet may be reached directly or via an intermediary subnet
- Backend service routes traffic to VCN through Service Gateway
Session Types
- Managed SSH session
- Target is Linux only with an OpenSSH server
- SSH port forwarding session
- Port forwarding (also known as SSH tunneling) creates a secure connection between a specific port on the client machine and a specific port on the target resource. Using this connection you can relay other protocols.
- Dynamic port forwarding session
- A dynamic port forwarding (SOCKS5) session has the same benefits of an SSH port forwarding session, but allows you to dynamically connect to any target resource in a private subnet. Unlike other session types that you configure to connect to a specific target resource (IP address or DNS name), with a dynamic port forwarding (SOCKS5) session you create a tunnel to a target subnet and the client decides which resource and port to connect to.
OCI Bastion Details
- Bastion
- 20 bastions per tenancy
- Session
- 5 sessions per bastion
- Session time
- 180 minutes maximum
- Assocaition
- Single VCN only
- Dependency
- Oracle agent must be running and the Bastion plugin is enabled
Usage of Resource Type: bastion-family
A policy to allow users in a group to create, update, and delete all Bastion resources (bastion-family) in entire tenancy (scope).
Allow group <group-name> to manage bastion-family in tenancy